By Mark Stam The Master File Table or MFT can be considered one of the most important files in the NTFS file system, as it keeps records of all files in a volume, the physical location. This video demonstrates how to mount a VM Image in FTK Imager.This could be useful for password enumeration during a pen test. If you are able to find vmdk f.
Ftk-imager
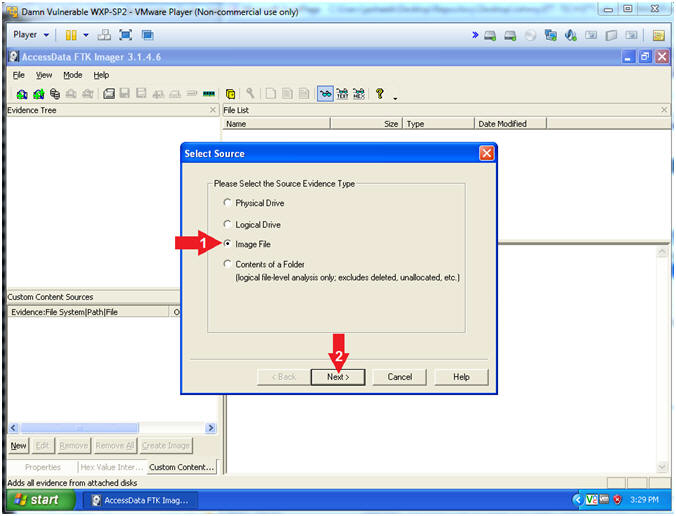
FTK® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence. After you create an image of the data, use Forensic Toolkit® (FTK®) to perform a thorough forensic examination and create a report of your findings. FTK Imager will:


FTK® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence. After you create an image of the data, use Forensic Toolkit® (FTK®) to perform a thorough forensic examination and create a report of your findings. There are other tools out there that can collect folder level items. If you want to retain MAC times and do not need an image container, you can try using Robocopy. It is easily scripted and preserves the MAC times. You can copy the folders to an external drive and then once you are able to, you can use FTK Imager GUI to collect the copied folder.
Create forensic images of local hard drives, CDs and DVDs, thumb drives or other USB devices, entire folders, or individual files from various places within the media.
Preview files and folders on local hard drives, network drives, CDs and DVDs, thumb drives or other USB devices.
Preview the contents of forensic images stored on the local machine or on a network drive.
Mount an image for a read-only view that leverages Windows® Internet Explorer® to see the content of the image exactly as the user saw it on the original drive.
Export files and folders from forensic images.
See and recover files that have been deleted from the Recycle Bin, but have not yet been overwritten on the drive.
Create hashes of files to check the integrity of the data by using either of the two hash functions available in FTK Imager: Message Digest 5 (MD5) and Secure Hash Algorithm (SHA-1).
Generate hash reports for regular files and disk images (including files inside disk images) that you can later use as a benchmark to prove the integrity of your case evidence. When a full drive is imaged, a hash generated by FTK Imager can be used to verify that the image hash and the drive hash match after the image is created, and that the image has remained unchanged since acquisition.
For details about FTK visit the product webpage.
588 West 400 South Suite 350


FTK® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence. After you create an image of the data, use Forensic Toolkit® (FTK®) to perform a thorough forensic examination and create a report of your findings. FTK Imager will:
FTK® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence. After you create an image of the data, use Forensic Toolkit® (FTK®) to perform a thorough forensic examination and create a report of your findings. There are other tools out there that can collect folder level items. If you want to retain MAC times and do not need an image container, you can try using Robocopy. It is easily scripted and preserves the MAC times. You can copy the folders to an external drive and then once you are able to, you can use FTK Imager GUI to collect the copied folder.
Create forensic images of local hard drives, CDs and DVDs, thumb drives or other USB devices, entire folders, or individual files from various places within the media.
Preview files and folders on local hard drives, network drives, CDs and DVDs, thumb drives or other USB devices.
Preview the contents of forensic images stored on the local machine or on a network drive.
Mount an image for a read-only view that leverages Windows® Internet Explorer® to see the content of the image exactly as the user saw it on the original drive.
Export files and folders from forensic images.
See and recover files that have been deleted from the Recycle Bin, but have not yet been overwritten on the drive.
Create hashes of files to check the integrity of the data by using either of the two hash functions available in FTK Imager: Message Digest 5 (MD5) and Secure Hash Algorithm (SHA-1).
Generate hash reports for regular files and disk images (including files inside disk images) that you can later use as a benchmark to prove the integrity of your case evidence. When a full drive is imaged, a hash generated by FTK Imager can be used to verify that the image hash and the drive hash match after the image is created, and that the image has remained unchanged since acquisition.
For details about FTK visit the product webpage.
588 West 400 South Suite 350
Ftk Imager For Windows
Lindon, UT 84042
Ftk Imager Guide
801.377.5410
Ftk Imager Install
© COPYRIGHT 2018 ACCESSDATA
